What Is Cloning In Cyber Security? Tips to Stay Safe from Clone in 2022?
Cloning In Cyber Security is typically achieved by malware infection.
Cloning, in the context of cyber security, is taking a legitimate document and changing its legitimate links with malicious links.
Clone phishing attacks can be tricky to spot at first look. That’s because they duplicate emails from credible companies using fake email addresses.
What is Cloning in Cyber Security?
It is the process of making and using an unauthorised clone of another person’s computer system to steal their data for fraud or spying reasons.
A subset of phishing is called clone phishing. It is an email that is a copy of one originally sent by an organisation. The recipient may receive this kind of email after they have initiated the contact, or it may be unsolicited.
Cloned emails might deceive users into disclosing information by making them seem real. The cybercriminal accesses private information through their fake website. Interestingly, it is designed to look exactly like the actual website.
Because hackers are more interested in the personal lives of high-profile people, clone phishing frequently targets them.
Statistics Cloning In Cyber Security
Phishing is the most common threat action connected to breaches, according to Verizon’s 2020 Data Breach Investigations Report.
In 2019, there were successful phishing attacks in 65% of US firms, according to Proofpoint’s 2020 State of the Phish study. This speaks volumes about the intelligence of attackers. The statistics also emphasise the importance of equally advanced security awareness training.
Clone Phishing vs Spear Phishing
Two of the most common forms of email attack are:
- Phishing
- Spear phishing
Both email attacks aim to fool you into taking a particular action, usually clicking on a malicious link or file. Targeting is primarily the difference between them.
Here are some of the contrasting features between clone and spear phishing:
| Clone phishing | Spear phishing |
| In Clone phishing, Hackers must first obtain an existing or already sent email to create a replica. | In spear phishing, Hackers use tactics to create the original email content. |
| Hackers frequently copy emails sent out in mass and send the cloned version in a group. | A single person or a very small group are often the only ones who receive spear phishing campaigns since they are so precisely targeted. |
| One such example: Your package has been delayed; click here for details, says an email that appears to be from a reputable delivery service. If you click the link, malware can be placed on your computer. Besides this, you might also visit a fake website where your name, address, and social security number are required. Then, fraud or identity theft might use that information, or it could be sold on the black market. | One such example: Let’s say you post online that you will be visiting Chicago soon. You might receive an email from a coworker suggesting you check out the menu at Joe’s Grill while you’re there. When you click the link, malware is installed on your computer while reading the menu. |
| Other Examples of clone phishing pretexts include: Providing sensitive access credentials in response to an email from “IT help.” Clicking a link for an urgent software update. Accessing a website through a link to claim a “gift” or “prize.” | Other Examples of Sphere phishing include Fake CEO The attacker will take over a similar email address to the employee, such as that of their employer’s CEO. Smishing a phishing scheme using SMS Vishing The victim will receive a call from an unknown caller and a voicemail asking them to call them back. |
Which one is more dangerous?
Beyond spear phishing, clone phishing is the next level in deceiving the recipient’s suspicions.
Users believe that the websites and domains they use are secure. In reality, though, customers are tricked by hackers who appear as legitimate websites and domains. Because it is difficult for victims to recognise a fake email, clone phishing attacks are considered the most dangerous.
One such example of clone phishing is illustrated in the following snapshot:
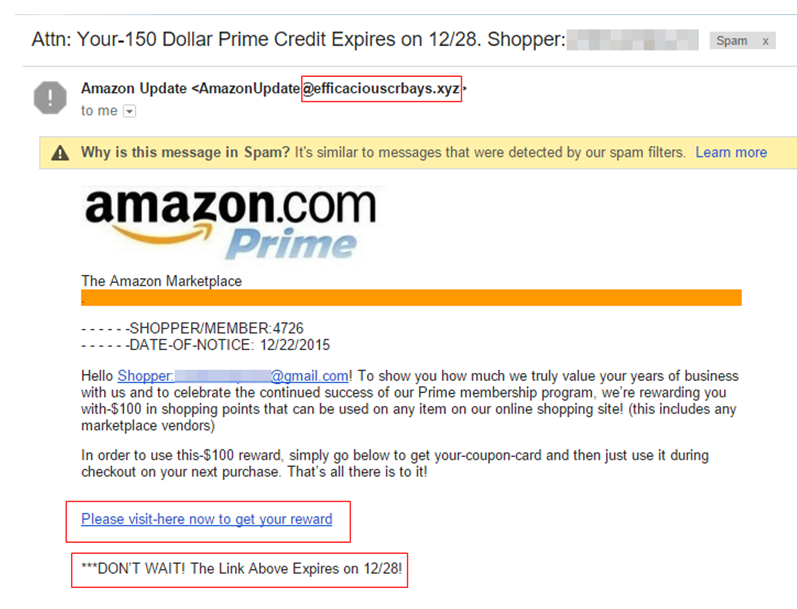
How to stay safe from Clone Phishing 2022?
It’s crucial to stay safe with security precautions to avoid falling victim to online scams and phishing attempts. You can protect your company against online fraud by using the following Cloning In Cyber Security advice:
- Secure Your Email Credentials
- Always examine the email message from the sender.
- Hover over any landing page links in emails to double-check their credibility.
- Follow up with the company that sent the email.
- Keep an eye out for odd errors, as cloned emails are not always genuine.
- Always provide your information to websites with an “HTTPS” prefix before the URL.
- Employee education about cyberattacks is essential for an organisation to be fully protected. They should be less exposed and more prepared to defend against new cyberattacks.
Secure your business by providing security awareness training for your staff. A thorough phishing awareness training can protect against phishing attacks, including spear phishing.
- You can check an email’s authenticity by contacting the sender via phone or text.
- Use anti-phishing technologies to prevent even the most sophisticated phishing attempts.
- Check emails for attachments and links to make sure they are legitimate.
- To protect the company’s digital assets, you must optimise your cyber defences. As cloning threats advance in sophistication, working with a competent industry partner like RSI Security is considerably simpler than optimising your cyber defences internally.
Also See: What Is SOC For Cybersecurity? Why Do You Need It?
Summary
Phishing attacks may cause irreparable harm to a company. Clone phishing attacks can be successfully mitigated by employee awareness. This, together with multi-layered security solutions, will yield beneficial outcomes.
You’ll be well on your way to preventing clone phishing if you have a strategy to strengthen your Cloning In Cyber Security.
FAQs
What is cloning IT security?
In IT, cloning is the method of taking a legitimate document and replacing its links with malicious links.
What is a Cloning In Cyber Security attack?
It is a phishing attack in which hackers fake genuine email messages from legitimate companies.

